So the year is nearly over, and I still haven't finished my blogs!
Been a busy December, so I have had no time to finish my Raspberry Pi blogs!
New years resolutions is to complete the RPi blogs and to move on to more in depth subject!
Happy New Year to anyone who reads my blog!
M
Monday, 31 December 2012
Tuesday, 13 November 2012
Transfering an image file to a SD card via Linux CLI
The objective for this blog is very straight forward, and the title should be self-explanatory. In my previous blog (here) I discussed downloading the distribution image file. (we used this one) I also explained how to unzip the image file.
The next step is to copy the image from your PC to your SD card.
Before I describe the process (all one command) it may proof useful to discuss what type of SD card to use.
Personally I don't like have a lump of SD sticking out of the side of my RPi, so one of my personal mod's is to get a Micro SD converter and use a Micro SD card instead.
These aren't that expensive and can be bought from ModMyPi. (I'd also suggest adding heatsinks, whist your in modification mode) ;-)
Now to the class of Micro SD... I have read in several forums that the class of SD make no difference when used with the Raspberry Pi. I tend to disagree. It is true that RPi's will work fine using the cheaper class 4 cards. It is also true that the class speeds listed refer to serial read\write speeds, and not the random nature of a RPi's file system. But with all that said, in my experience, and by only using two RPi's side by side I personally felt that using a class 10 Sandisk Micro SD was noticeably faster than using a cheap ADATA class 4 Micro SD card.(my only benchmarking test was to watch them booting. The hardware is the same, but each time I tried, the Sandisk RPi gave me the log on prompt first!)
This really falls down to personal choice, and I confess to buying several of the class 4 cards as my local Maplin's had them on offer. ;o) Annoyingly, there are now selling 32G class 10 cards for the same price; here.
So back to the image file, you should now have the unzipped image file in the directory your working in.
You can check this with "pwd"
You can also check the file name of your image using the "ls" command.
We are now ready to transfer this image to our SD card (or MicroSD in my case).
First we need to identify the device name given to our card.
To do this, enter the "df" command, but instead of looking at the space being used, look at the volumes mounted. (df is a command to display the free disk space).
Adding the "-h" makes the results human readable.
If you run the command before inserting you SD card, and then again after what ever volumes are new are related to you SD card.
If you look at the second "df -h" you'll notice the highlighted is "/dev/mmcblk0".
This is the device name for your SD card. Sometimes if you have partitions on your SD card you may find it ends with "p0" or "p1". This is how Linux identifies partitions. We are only interested in the volumes device name as we have partitions within our image file.
You will need to unmount this partition before we start the transfer.
If you have multiply partitions, add p0 or p1 or whatever partions you have and unmount each partition.
You can check again with the "df -h" command
Now to the image transfer.
*********************************************************************************************************************************
Warning, you can damage you working PC if you get this command incorrect! be very very careful!
*********************************************************************************************************************************
The "dd" command follows the following format ;
In my example I typed "sudo dd bs=1M if=/home/anon/RaspberryPi/2012-10-28-wheezy-raspbian.img of=/dev/mmcblk0"
If we break that down, it contains the following;
"sudo" This command should be run with root privileges.
"dd" Data Destroyer!! you have been warned! :-p Seriously, I have no idea why dd, probably because cc was already used in C. But for us, this is the command we're executing!
"bs-1M" this is the byte size. you could try 4M, or if you've lots of spare time try reducing the size. With the 4G file we're using, I find 1M chunks works fine, but does take a little while. (gives me time to write this blog) ;-)
"if=/home/anon/RaspberryPi/2012-10-28-wheezy-raspbian.img" is the location of your image file. it is important to get the absolute location. I've included my '/home/username/filedirectory' to make it easier to understand instead of using '~/filedirectory'
"of=/dev/mmcblk0" is the location we're copying our image file to... basically the volumes device name. we identified this earlier using the "df" command.
If you get your "if" and "of" the wrong way around, you will be copying the contents of your SD card onto your harddrive. (great for backing up your RPi, but risky if you get your absolute locations wrong!)
Once this process starts, be patient! transfering 4G in 1M chunks can take a while, so go do some light reading.
I suggest looking here as they do a much better job of explaining this than me.
My next blog will discuss that all important first boot!
The next step is to copy the image from your PC to your SD card.
Before I describe the process (all one command) it may proof useful to discuss what type of SD card to use.
Personally I don't like have a lump of SD sticking out of the side of my RPi, so one of my personal mod's is to get a Micro SD converter and use a Micro SD card instead.
These aren't that expensive and can be bought from ModMyPi. (I'd also suggest adding heatsinks, whist your in modification mode) ;-)
Now to the class of Micro SD... I have read in several forums that the class of SD make no difference when used with the Raspberry Pi. I tend to disagree. It is true that RPi's will work fine using the cheaper class 4 cards. It is also true that the class speeds listed refer to serial read\write speeds, and not the random nature of a RPi's file system. But with all that said, in my experience, and by only using two RPi's side by side I personally felt that using a class 10 Sandisk Micro SD was noticeably faster than using a cheap ADATA class 4 Micro SD card.(my only benchmarking test was to watch them booting. The hardware is the same, but each time I tried, the Sandisk RPi gave me the log on prompt first!)
This really falls down to personal choice, and I confess to buying several of the class 4 cards as my local Maplin's had them on offer. ;o) Annoyingly, there are now selling 32G class 10 cards for the same price; here.
You can check this with "pwd"
You can also check the file name of your image using the "ls" command.
We are now ready to transfer this image to our SD card (or MicroSD in my case).
First we need to identify the device name given to our card.
To do this, enter the "df" command, but instead of looking at the space being used, look at the volumes mounted. (df is a command to display the free disk space).
Adding the "-h" makes the results human readable.
If you run the command before inserting you SD card, and then again after what ever volumes are new are related to you SD card.
If you look at the second "df -h" you'll notice the highlighted is "/dev/mmcblk0".
This is the device name for your SD card. Sometimes if you have partitions on your SD card you may find it ends with "p0" or "p1". This is how Linux identifies partitions. We are only interested in the volumes device name as we have partitions within our image file.
You will need to unmount this partition before we start the transfer.
unmount /dev/mmcblk0
If you have multiply partitions, add p0 or p1 or whatever partions you have and unmount each partition.
You can check again with the "df -h" command
Now to the image transfer.
*********************************************************************************************************************************
Warning, you can damage you working PC if you get this command incorrect! be very very careful!
*********************************************************************************************************************************
The "dd" command follows the following format ;
dd if=<source> of=<target> bs=<byte size>
In my example I typed "sudo dd bs=1M if=/home/anon/RaspberryPi/2012-10-28-wheezy-raspbian.img of=/dev/mmcblk0"
If we break that down, it contains the following;
"sudo" This command should be run with root privileges.
"dd" Data Destroyer!! you have been warned! :-p Seriously, I have no idea why dd, probably because cc was already used in C. But for us, this is the command we're executing!
"bs-1M" this is the byte size. you could try 4M, or if you've lots of spare time try reducing the size. With the 4G file we're using, I find 1M chunks works fine, but does take a little while. (gives me time to write this blog) ;-)
"if=/home/anon/RaspberryPi/2012-10-28-wheezy-raspbian.img" is the location of your image file. it is important to get the absolute location. I've included my '/home/username/filedirectory' to make it easier to understand instead of using '~/filedirectory'
"of=/dev/mmcblk0" is the location we're copying our image file to... basically the volumes device name. we identified this earlier using the "df" command.
If you get your "if" and "of" the wrong way around, you will be copying the contents of your SD card onto your harddrive. (great for backing up your RPi, but risky if you get your absolute locations wrong!)
Once this process starts, be patient! transfering 4G in 1M chunks can take a while, so go do some light reading.
I suggest looking here as they do a much better job of explaining this than me.
My next blog will discuss that all important first boot!
Thursday, 1 November 2012
Raspberry Pi Madness...
When my first Raspberry Pi (RPi)was finally delivered, I decided I wasn't going to blog too much about it. There are plenty of well written, and self explanatory blogs out there which are very helpful and informative.
Since then, I have ordered two more RPi's and tried various distributions.
Whilst playing, I found there were certain tasks which I performed on every build regardless of the distribution.
During a conversation with a friend, the only other RPi owner I know personally (We geeks are a rare breed) I realised that some of the tasks I consider run of the mill may not be that obvious to some people.
So the objective of this blog is to discuss some of the steps I take when I first build a new image on the RPi. To keep things simple, I'm going to use the Rasbian image as an example, but most of these steps are applicable to other distributions. (also on other Linux based machines).
First some ground rules, I have written this blog from my home point of view. Personally I no longer use Windows on any of the machines I own. (my work laptop belongs to my company, so is the exception.) Therefore all my set-up steps are performed on Linux based machines. If you intend to follow this blog as a guide, you will need to use Linux PC. If you don't currently have one, I suggest searching for one of the many LiveCD distributions or create a Linux image on a USB drive.(http://www.pendrivelinux.com/)
If not, refer to one of the many other guides aimed at Windows users.
Also to avoid this turning into a mammoth blog, I'm going to fragment it into sections.
This section will cover downloading your image file. ;-)
So for this you can open your favourite browser and go to the downloads page and select your preferred image.
At the time of writing, this is currently found here;
http://downloads.raspberrypi.org/images/raspbian/2012-10-28-wheezy-raspbian/2012-10-28-wheezy-raspbian.zip
Once you down load the file, it is always a good idea to check you downloaded the file without any errors. You can do this with the following command;
sha1sum ~/2012-10-28-wheezy-raspbian.zip
This will give you a checksum value which you can check against the download directory.
For the supplied image it should be;
SHA-1 3ee33a94079de631dee606aebd655664035756be
This also confirms to important facts, 1) the file was downloaded correctly. 2) the file is the same as the file uploaded by the image provider.
It is possible to skip this step, but it can save time later if you know your image file is not corrupt!
Next, it is VERY important you know where this file is located.
I normally transfer the zipped file to a raspberry directory in my home folder.
My directory path is ~/RaspberryPi/
You will need to know this when we transfer the image to a SD card, but for now we need to unzip the image file. This can be done using the "extract here" option in your file manager (nautilus) but I prefer to do things in CLI as shown below;
For those of you who like to cut + paste the command is;
unzip 2012-10-28-wheezy-raspbian.zip
at this point you should have the 2012-10-28-wheezy-raspbian.img file in you ~/RaspberryPi/ directory.
Now we need to get this image onto a SD card. I'll cover this off in my next blog.
Since then, I have ordered two more RPi's and tried various distributions.
Whilst playing, I found there were certain tasks which I performed on every build regardless of the distribution.
During a conversation with a friend, the only other RPi owner I know personally (We geeks are a rare breed) I realised that some of the tasks I consider run of the mill may not be that obvious to some people.
So the objective of this blog is to discuss some of the steps I take when I first build a new image on the RPi. To keep things simple, I'm going to use the Rasbian image as an example, but most of these steps are applicable to other distributions. (also on other Linux based machines).
First some ground rules, I have written this blog from my home point of view. Personally I no longer use Windows on any of the machines I own. (my work laptop belongs to my company, so is the exception.) Therefore all my set-up steps are performed on Linux based machines. If you intend to follow this blog as a guide, you will need to use Linux PC. If you don't currently have one, I suggest searching for one of the many LiveCD distributions or create a Linux image on a USB drive.(http://www.pendrivelinux.com/)
If not, refer to one of the many other guides aimed at Windows users.
Also to avoid this turning into a mammoth blog, I'm going to fragment it into sections.
This section will cover downloading your image file. ;-)
So for this you can open your favourite browser and go to the downloads page and select your preferred image.
At the time of writing, this is currently found here;
http://downloads.raspberrypi.org/images/raspbian/2012-10-28-wheezy-raspbian/2012-10-28-wheezy-raspbian.zip
Once you down load the file, it is always a good idea to check you downloaded the file without any errors. You can do this with the following command;
sha1sum ~/2012-10-28-wheezy-raspbian.zip
This will give you a checksum value which you can check against the download directory.
For the supplied image it should be;
SHA-1 3ee33a94079de631dee606aebd655664035756be
This also confirms to important facts, 1) the file was downloaded correctly. 2) the file is the same as the file uploaded by the image provider.
It is possible to skip this step, but it can save time later if you know your image file is not corrupt!
Next, it is VERY important you know where this file is located.
I normally transfer the zipped file to a raspberry directory in my home folder.
My directory path is ~/RaspberryPi/
You will need to know this when we transfer the image to a SD card, but for now we need to unzip the image file. This can be done using the "extract here" option in your file manager (nautilus) but I prefer to do things in CLI as shown below;
For those of you who like to cut + paste the command is;
unzip 2012-10-28-wheezy-raspbian.zip
at this point you should have the 2012-10-28-wheezy-raspbian.img file in you ~/RaspberryPi/ directory.
Now we need to get this image onto a SD card. I'll cover this off in my next blog.
Sunday, 7 October 2012
Raspberry Pi Wallpaper
Back in August, I ordered myself a Model B Raspberry Pi. In late September it finally arrived.
I have since spent a large part of my free time playing with it.
I've played with quite a few distributions, I've created PBX's using Asterisk, a media center, a dropbox (not "Dropbox! although I have played with the api's), and even a device running metasploit. (on both my own, and on the pwnpi image).
I've written a few scripts which I may blog about at a later date, but what this blog is about is my personal wallpaper;
I have since spent a large part of my free time playing with it.
I've played with quite a few distributions, I've created PBX's using Asterisk, a media center, a dropbox (not "Dropbox! although I have played with the api's), and even a device running metasploit. (on both my own, and on the pwnpi image).
I've written a few scripts which I may blog about at a later date, but what this blog is about is my personal wallpaper;
This wallpaper is the combination of an existing wallpaper I found on the Raspberry Pi Forum and an older one I've been using for years after finding it on the DeviantArt website.
For those who aren't familiar, it is a reference to the hacker manifesto written by +++The Mentor+++ back in 1986.
Feel free to use this Wallpaper.
p.s. checkout the 1337 time stamp for this post... LOL
Friday, 7 September 2012
Another simple PING script using tcl on a Cisco router
In a previous blog I discussed using tcl to create a simple script to ping multiply IP addresses from a Cisco router. (http://garnersguides.blogspot.co.uk/2012/08/some-clever-ping-tricks.html)
In this blog I have embed a video I created which describes a variation to the original script using a conditional loop.
If you have any questions, please feel free to ask me.
In this blog I have embed a video I created which describes a variation to the original script using a conditional loop.
If you have any questions, please feel free to ask me.
Wednesday, 29 August 2012
Creating multiple Loopback addresses using a Tcl script
In a previous blog, (Some clever PING tricks) I discussed using Tcl to create PING scripts to ping multiple hosts. This got me thinking, what other cool applications can I demonstrate using Tcl.
The first thing to spring to mind was creating multiple Loopback addresses. The aim of this blog is to discuss how to create multiply Loopback addresses on a router using a Tcl script.
"Why would you want to create loads of loopback addresses?" I hear you ask...
When testing routing protocols in a lab environment (Especially BGP) it is good to have plenty of routes in your routing table. Rather than create loads of routers in GNS3, or fill a rack with kit you don't need, it is easier to simulate other networks using Loopback address on a Router and then add them to our routing protocol. That's not the objective of this blog, this blog is to discuss how to create them.
As with the PING script, I will start by saying you could write all your loopbacks in a word document, and then cut them into your router, but doing it this way, only takes one line of code. (although, I may split it up to make it easier to understand).
The last PING script used the for command to create what in programming terms is called a Control Flow Loop.
The correct syntax is;
for init test body
Or if we display this in a Tcl command it would look like this;
for { init } { test } { next } {
Look familiar?
for { set i 1 } {$i <= 9 } {incr i } {
ping 10.0.0.$i re 10 si 1500 so lo0 df-bit
}
This was our last PING script in the last blog.
By changing our variable, and adapting the body we can use this loop to create our loopback addresses.
for { set i 0 } {$i <= 255 } { incr i } {
So what I've done now is "set" "i" (our variable) at 0.
The conditional test is to make sure "i" is less than 255. We can't have an octet in a IP address greater than 255.
We then increment "i" by one each time the loop is run.
Finally we use the "puts" command to send data to the router.
As we are now using configuration commands on our router so we need to use "ios_config" rather than the "exec" we used in our other PING script.
The commands should be self-explanatory;
ip address 10.255.$i.255 255.255.255.255 Is to create the IP address. I have chosen to put our variable in the third octet, but in theory we could place it in different octets, or even in several octets.
We can test our script by looking at our interfaces with the "show ip interface brief" command;
I hope this blog has been of interest, and helped you understand a little more about the power of scripting!
The first thing to spring to mind was creating multiple Loopback addresses. The aim of this blog is to discuss how to create multiply Loopback addresses on a router using a Tcl script.
"Why would you want to create loads of loopback addresses?" I hear you ask...
When testing routing protocols in a lab environment (Especially BGP) it is good to have plenty of routes in your routing table. Rather than create loads of routers in GNS3, or fill a rack with kit you don't need, it is easier to simulate other networks using Loopback address on a Router and then add them to our routing protocol. That's not the objective of this blog, this blog is to discuss how to create them.
As with the PING script, I will start by saying you could write all your loopbacks in a word document, and then cut them into your router, but doing it this way, only takes one line of code. (although, I may split it up to make it easier to understand).
The last PING script used the for command to create what in programming terms is called a Control Flow Loop.
The correct syntax is;
for init test body
Or if we display this in a Tcl command it would look like this;
for { init } { test } { next } {
body
}
Look familiar?
for { set i 1 } {$i <= 9 } {incr i } {
ping 10.0.0.$i re 10 si 1500 so lo0 df-bit
}
This was our last PING script in the last blog.
By changing our variable, and adapting the body we can use this loop to create our loopback addresses.
for { set i 0 } {$i <= 255 } { incr i } {
puts [ ios_config "interface loopback$i" "ip address 10.255.$i.255 255.255.255.255" ]
}
So what I've done now is "set" "i" (our variable) at 0.
The conditional test is to make sure "i" is less than 255. We can't have an octet in a IP address greater than 255.
We then increment "i" by one each time the loop is run.
Finally we use the "puts" command to send data to the router.
As we are now using configuration commands on our router so we need to use "ios_config" rather than the "exec" we used in our other PING script.
The commands should be self-explanatory;
interface loopback$i Is the IOS command to create a loopback interface. We use "$i" our variable to change the loopback each time the script loops.
ip address 10.255.$i.255 255.255.255.255 Is to create the IP address. I have chosen to put our variable in the third octet, but in theory we could place it in different octets, or even in several octets.
(I.E. 10.255.$i.$i)
We can test our script by looking at our interfaces with the "show ip interface brief" command;
No point showing all 255 loopbacks, but just to prove I didn't cheat, here is the end of that show ip interface brief command;
Our script worked and we have just created 255 loopbacks with a single line of Tcl scripting.
I hope this blog has been of interest, and helped you understand a little more about the power of scripting!
Tuesday, 28 August 2012
Tip for remote working on Cisco devices.
It's not uncommon to find yourself working of Cisco devices remotely. Recently I have been working on a project where the Cisco hardware has been all over the planet.
When configuring equipment remotely, you should always make sure you're not going to cut off your remote connection. Even the most experienced Engineer can inadvertently isolate a router or switch.
And sometimes, it can take a while to get some on site assistance.
One method I have employed involves using the reload command.
Before describing the process it is important to understand that this tip should only be employed on hardware which does NOT have live traffic on it. Or if it has, make sure you complete your changes in a correct outage window.
So the tip… use the reload command!
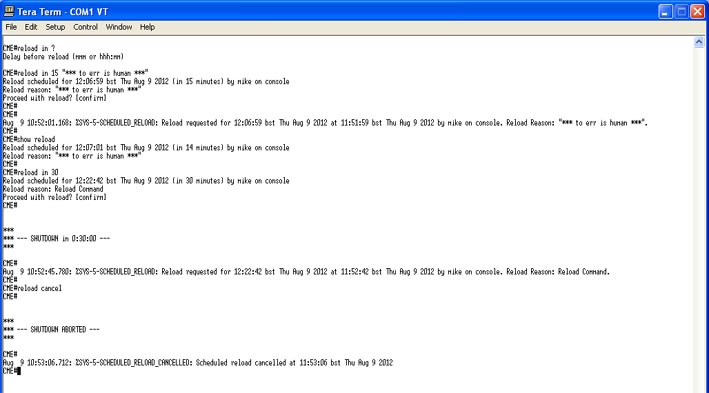
The 'reload' command is self-explanatory, but it can also be used with a timer.
You can set the reload to happen at a predefined date\time as shown below;
The command is "reload at TI:ME Day Month" or "reload at TI:ME Month Day".
You can then add a text message for the reason. In my example I used "*** Scheduled reload by Mike ***".
To cancel you're scheduled use the "reload cancel" command.
Obviously waiting 13hours for our reload is not ideal, so the version I prefer is the "reload in mmm" command shown below;
My first example was to get the router to reload in 15 minutes. "reload in 15 TEXT MESSAGE HERE"
You can check the reload with the "show reload" command.
If you need to extend your reload time, you can simply use the command again with your new time frame. I.E. "reload in 30"
As before, you can cancel it with the "reload cancel" command.
Remember to save your configuration after you've made any changes… and DON'T forget to cancel the reload if it isn't required!
One last tip, don't accidentally type reload and hit return several times… can be a costly mistake!
"From the errors of others, a wise man corrects his own." ~Syrus
When configuring equipment remotely, you should always make sure you're not going to cut off your remote connection. Even the most experienced Engineer can inadvertently isolate a router or switch.
And sometimes, it can take a while to get some on site assistance.
One method I have employed involves using the reload command.
Before describing the process it is important to understand that this tip should only be employed on hardware which does NOT have live traffic on it. Or if it has, make sure you complete your changes in a correct outage window.
So the tip… use the reload command!
The 'reload' command is self-explanatory, but it can also be used with a timer.
You can set the reload to happen at a predefined date\time as shown below;
The command is "reload at TI:ME Day Month" or "reload at TI:ME Month Day".
You can then add a text message for the reason. In my example I used "*** Scheduled reload by Mike ***".
To cancel you're scheduled use the "reload cancel" command.
Obviously waiting 13hours for our reload is not ideal, so the version I prefer is the "reload in mmm" command shown below;
My first example was to get the router to reload in 15 minutes. "reload in 15 TEXT MESSAGE HERE"
You can check the reload with the "show reload" command.
If you need to extend your reload time, you can simply use the command again with your new time frame. I.E. "reload in 30"
As before, you can cancel it with the "reload cancel" command.
Remember to save your configuration after you've made any changes… and DON'T forget to cancel the reload if it isn't required!
One last tip, don't accidentally type reload and hit return several times… can be a costly mistake!
"From the errors of others, a wise man corrects his own." ~Syrus
Some clever PING tricks
As a Network Engineer, using PING is something that you can sometimes take for granted. We probably all use it, for basic troubleshooting, and never really give it much of a thought.
The aim of this blog is to have a think about PING, and show some clever tricks I have employed using PING on Cisco routers.
Most people who use PING simple use the simplest form; PING <IP address> as shown below;
As you can see from the image above, a basic PING sends 5 ICMP echo requests which are 100 bytes in size.
Sometime people may change this by using an extended PING.
You need to be in privileged EXEC mode to use the extended PING commands. Just type "ping" and press return to start an extended ping as shown below;
As you can see from the above image, with the extended PING we have sent 10 ICMP echo requests which were 1500 bytes in size.
We also changed our timeout to 5 seconds.
Using extended PINGs is well known, and probably as far as most people take PING.
However, since IOS12.x Cisco has made the extended PING commands available in a single command.
We can repeat the above example in one command "ping ip 10.0.0.1 repeat 10 size 1500 timeout 5" as shown below;
By default, the PING will adopt the IP address of the interface from which it leaves the router. Sometimes we want to change this (like when pinging within a particular VLAN you would adopt the source interface of the sub-interface associated with that VLAN). This is also done using extended pings, but now we've learn't to complete extended pings in a single line, lets demonstrate it;
So as you can see from the image above, this PING was sent from our router using the IP address of Loopback 0 or 1.1.1.1
When using a source port for your PINGs it is important to consider your routing tables. Just because you have a route to your destination... does your destination have a route back to your source port?
The aim of this blog is to have a think about PING, and show some clever tricks I have employed using PING on Cisco routers.
Most people who use PING simple use the simplest form; PING <IP address> as shown below;
As you can see from the image above, a basic PING sends 5 ICMP echo requests which are 100 bytes in size.
Sometime people may change this by using an extended PING.
You need to be in privileged EXEC mode to use the extended PING commands. Just type "ping" and press return to start an extended ping as shown below;
As you can see from the above image, with the extended PING we have sent 10 ICMP echo requests which were 1500 bytes in size.
We also changed our timeout to 5 seconds.
Using extended PINGs is well known, and probably as far as most people take PING.
However, since IOS12.x Cisco has made the extended PING commands available in a single command.
We can repeat the above example in one command "ping ip 10.0.0.1 repeat 10 size 1500 timeout 5" as shown below;
By default, the PING will adopt the IP address of the interface from which it leaves the router. Sometimes we want to change this (like when pinging within a particular VLAN you would adopt the source interface of the sub-interface associated with that VLAN). This is also done using extended pings, but now we've learn't to complete extended pings in a single line, lets demonstrate it;
So as you can see from the image above, this PING was sent from our router using the IP address of Loopback 0 or 1.1.1.1
When using a source port for your PINGs it is important to consider your routing tables. Just because you have a route to your destination... does your destination have a route back to your source port?
Just to round up on extended PING's, another useful command is the DF-bit. this can be used to ensure your PING does not get fragmented.
On Ethernet interfaces, the maximum MTU size is usually 1500 bytes. We can check this with the "show interface fastethernet 0/0" command;
FastEthernet0/0 is up, line protocol is up
Hardware is Gt96k FE, address is c000.1400.0000 (bia c000.1400.0000)
Internet address is 192.168.0.1/30
MTU 1500 bytes, BW 100000 Kbit/sec, DLY 100 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation ARPA, loopback not set
Keepalive set (10 sec)
Full-duplex, 100Mb/s, 100BaseTX/FX
So in theory the maximum size packet we can send with out using fragmentation is 1500 bytes.
We can check this using extended PING's as shown below;
Our first PING has a MTU size of 1500 bytes, which we would expect to work without the need for fragmentation.
Our second PING has a MTU of 1501 bytes, which has exceed the maximum allowed on the interface. Therefore in order for this PING to be successful, we would need to fragment it. Which is exactly what the router will do, and is why this PING also works.
In our final PING we have enabled the "df-bit" which basically tells the router do not fragment me. We've also made sure the MTU is above 1500 bytes. Therefore this PING fails as it is too large for the interface, and can't be fragmented.
So now for the clever bit;
Since IOS 12.3(2)T Cisco routers have introduced Scripting with Tcl. What has this got to do with PING I hear you ask....
Well we can use Tcl to write PING scripts to PING multiple destinations, and using what we've just learn't above, we can do clever extended PINGs.
Let's assume we want to PING 9 different devices, we could enter the ping command 9 times with all of our destination addresses. (In fact, that is exactly what I used to do before I discovered Tcl). We could write out our PING commands in a text document, and cut and paste them into our router, but that isn't using Tcl and isn't that clever.
Instead, we can write a short script to do that for us.
Before we look at a PING script, I think it is important to point out a few things we need to considered when scripting (or programming).
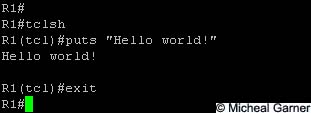
puts If your a old enough to remember the BBC basic PC, you may well remember the print command.
In Tcl the puts command does roughly the same thing. It can send a string of data out of a channel. Normally to stdout which to you and I means to the screen.
So our first ever Tcl script should be the classic "hello world!" script.
Notice the quotation marks around the Hello world!. These are important, as the command will read the spaces as delimiters.
Congratulations! If your following this blog, you've just written your first Tcl script!
In fact lets create a variable now...
Mikesvariable = 1
Now we've decided what Mikesvariable is (1) lets use it in a small Tcl script.
As you can see, we set our variable with the "set" command.
If we try printing our variable to the screen using the puts command we get the contents of the variable (1).
If we don't put the "$" symbol in front of the variable, we get Mikesvariable.
This is an IMPORTANT programming concept. The $ symbol is used to identify variables.
We can now use what we've learnt to combine the two concepts and re-create our Hello world script like this;
So as you can see, variables can be quite useful.
I don't want to turn this blog into a programming lesson, but I recommend having a good google about using variables, as manipulating them, is what makes scripting such a powerful tool.
The next programming concept we need to quickly cover is loops! We can implement loop a simple loop using the foreach command.
The easiest example I can think of is our first actual PING script.
We need to create a list of IP address's and we want to issue the PING command for each one.
To do this in Tcl, we can start by creating our list of IP addresses. So our script will look like this;
R1#tclsh
R1(tcl)#foreach IPAddress {
+>(tcl)#10.0.0.1
+>(tcl)#10.0.0.2
+>(tcl)#10.0.0.3
+>(tcl)#} { puts [ exec "ping $IPAddress" ] }
What this basic script is doing is creating a list of variables called $IPAddress.
The puts command is the same as in our "Hello world!" script, but is using the contents of the [brackets].
The exec is a command to run Cisco commands with privileged mode characteristics. The inside of the "quotes" is the actual command we're going to use.
So basically the script will enter ping $IPAddress into the cli of the router. The content of the $IPAddress variable will be the contents of our list. The first set of {brackets}.
Which in our example is 10.0.0.1, 10.0.0.2 and 10.0.0.3.
We run our script by pressing enter after the last set of "}"
As you can see, we've just run our first example of a simple PING script.
We could adapt our $IPAddress list to match our required IP addresses, and use this script on various routers.
That said, this script isn't using any of our extended PING commands discussed earlier...
So lets rewrite our script to increase our MTU size to 1500 bytes, and to use a Source interface of Loopback 0 and to set the DF-bit so we have a fragment free PING to our three addresses and send 10 PINGs.
R1(tcl)#foreach IPAddress {
+>(tcl)#10.0.0.1
+>(tcl)#10.0.0.2
+>(tcl)#10.0.0.3
+>(tcl)#} { puts [ exec "ping ip $IPAddress rep 10 size 1500 source lo0 df-bit" ] }
+>(tcl)#10.0.0.1
+>(tcl)#10.0.0.2
+>(tcl)#10.0.0.3
+>(tcl)#} { puts [ exec "ping ip $IPAddress rep 10 size 1500 source lo0 df-bit" ] }
Type escape sequence to abort.
Sending 10, 1500-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Packet sent with the DF bit set
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 20/55/172 ms
Sending 10, 1500-byte ICMP Echos to 10.0.0.1, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Packet sent with the DF bit set
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 20/55/172 ms
Type escape sequence to abort.
Sending 10, 1500-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Packet sent with the DF bit set
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 20/32/48 ms
Sending 10, 1500-byte ICMP Echos to 10.0.0.2, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Packet sent with the DF bit set
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 20/32/48 ms
Type escape sequence to abort.
Sending 10, 1500-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Packet sent with the DF bit set
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 16/35/72 ms
Sending 10, 1500-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
Packet sent with the DF bit set
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 16/35/72 ms
Perfect!! As you can see, our script has taken shape, and is really starting to work for us!
Hopefully your now starting to see the advantages, of running PINGs using a Tcl script... but, If your mind works like mine, your probably thinking "well why not just cut and paste all your PING commands into the router and skip all this scripting stuff!" Well to answer that question, let me show you another way of repeating the above script, but using a lot less code, and doing more to our variable;
Hopefully your now starting to see the advantages, of running PINGs using a Tcl script... but, If your mind works like mine, your probably thinking "well why not just cut and paste all your PING commands into the router and skip all this scripting stuff!" Well to answer that question, let me show you another way of repeating the above script, but using a lot less code, and doing more to our variable;
R1#tclsh
R1(tcl)#for { set i 1 } {$i <= 9 } {incr i } {
+>(tcl)#ping 10.0.0.$i re 10 si 1500 so lo0 df-bit }
First of all, instead of using a foreach command, I'm using a for command for my loops.
I'm using increments to increase my variable ($i) and I continue to increase it, as long as it is less than 9.
So effectively, I'm pinging every address from 10.0.0.1 to 10.0.0.9. We could change our variable or increment, and could ping every address in a subnet.
We could also place our variable in a different octet. Ohh the power of scripts!! :-D
Here is a screen shot of the above script entered onto my router;
The last of the PINGS were cut off, but basically two lines of Tcl was enough to complete 9 extended PINGs to different IP addresses.
That is why we're using Tcl, and not just cut and paste!!
I hope you've enjoyed this blog, and found it useful. I also hope I've encouraged you to think a little deeper about how we use simple commands like PING.
Thursday, 19 April 2012
Decrypting Cisco type 7 passwords on a router
It is common knowledge that Cisco type 7 passwords are not secure.
A quick search on Google brings up plenty of websites that will crack the passwords for you, and a few scripts\tools you can run locally to get the type 7 password.
You can also decrypt the password on the router.
The aim of this blog is to describe the process for decrypting a type 7 password on router using just IOS commands.
First create a password on your router which you want to crack.
For my example I have created the password "cisco".
So the running configuration looks like this;
Remember when creating password on a router to use the "secret" keyword to ensure MD5 is used as type 7 passwords are not designed to be secure!
For further information, please refer to www.cisco.com
A quick search on Google brings up plenty of websites that will crack the passwords for you, and a few scripts\tools you can run locally to get the type 7 password.
You can also decrypt the password on the router.
The aim of this blog is to describe the process for decrypting a type 7 password on router using just IOS commands.
First create a password on your router which you want to crack.
For my example I have created the password "cisco".
So the running configuration looks like this;
password 7 1511021F0725
To
decrypt you password, first enter global configuration, then enter the
command "key chain test" followed by "key 1" then enter "key-string 7
1511021F0725" as shown
below;
As you can see from the screen shot above,
to show the password use the "show key chain test" command which will decrypt your
type 7 password key-string.Remember when creating password on a router to use the "secret" keyword to ensure MD5 is used as type 7 passwords are not designed to be secure!
For further information, please refer to www.cisco.com
Wednesday, 4 April 2012
Reading a pgp encrypted message from Linux CLI
If you've been following my PGP\GPG blogs, you should now have PGPGPG
installed on your Linux PC.
You will also have generated a PGP key and exported the Public Key, and then created an encrypted message for "Your Mate"
If not, please read the previous blogs installing pgpgpg, exporting public key and Encrypting a message.
All that remains is to read an encrypted message. That is the objective of this blog.
First you need to recieve an encrypted message. For this blog, I have created a message which was encrypted using "Your Name's" public key.
The message was placed in my home folder and was called "secretmessage.txt.asc" as shown below.
Check the contents of the file with the cat command.
As you can see, the content of the file are encrypted.
To decrypt the file use the "gpg --decrypt secretmessage.txt.asc" command.
You will be prompted for the passphrase. Then the encrypted message will be displayed.
Of course this is fine for a short message as shown, but if your message is larger you may want to extract it as a file.
This can be done using the "--output <filename>" command.
I have decrypted the "secretmessage.txt.asc" file again below, but this time I've saved the output to a file called secretmessage.txt.
Notice in the second "ls" there is a new file called "secretmessage.txt".
This is the content of the encrypted file. You can check this using the cat command as shown below.
Remember that this file may contain sensitive information, so storing it as a plain text file might not be a great idea.
I hope these blogs have been of use.
You will also have generated a PGP key and exported the Public Key, and then created an encrypted message for "Your Mate"
If not, please read the previous blogs installing pgpgpg, exporting public key and Encrypting a message.
All that remains is to read an encrypted message. That is the objective of this blog.
First you need to recieve an encrypted message. For this blog, I have created a message which was encrypted using "Your Name's" public key.
The message was placed in my home folder and was called "secretmessage.txt.asc" as shown below.
Check the contents of the file with the cat command.
As you can see, the content of the file are encrypted.
To decrypt the file use the "gpg --decrypt secretmessage.txt.asc" command.
You will be prompted for the passphrase. Then the encrypted message will be displayed.
Of course this is fine for a short message as shown, but if your message is larger you may want to extract it as a file.
This can be done using the "--output <filename>" command.
I have decrypted the "secretmessage.txt.asc" file again below, but this time I've saved the output to a file called secretmessage.txt.
Notice in the second "ls" there is a new file called "secretmessage.txt".
This is the content of the encrypted file. You can check this using the cat command as shown below.
Remember that this file may contain sensitive information, so storing it as a plain text file might not be a great idea.
I hope these blogs have been of use.
Monday, 2 April 2012
Importing a public key to your keyring and creating an encrypted message in Linux CLI
If you've been following my PGP\GPG blogs, you should now have PGPGPG
installed on your Linux PC.
You will also have generated a PGP key and exported the Public Key.
If not, please read the previous blogs installing pgpgpg and exporting public key
This blog aims to explain how to import someone else's key, and then send them an encrypted message.
Before we progress any further, you need to have someones Public Key. This can be acquired by email, downloading of a website, or passed via any means, but it is important that you trust the public key you have is from who you think it is from.
I have acquired a public key from "Your Mate" and have it in my home folder.
I first check the contents of my Key ring using the "gpg --list-key" command as shown below.
If you've been following my blogs in order, you should find the only key you have is the one you've generated.
Import the public key for the person you wish to send the encrypted message to with the "gpg --import keyname" command as shown below. As you can see, the key I imported was called "YourMate.asc"
You can confirm the key is now on your keyring by repeating the "gpg --list-key" command as shown above. Notice you now have the "Your Mate" key.
You can check that you have imported the correct public key by asking the owner to confirm the keys finger print.
This can be done using the "gpg --fingerprint" command to see all your keys fingerprints, or an individual key using any of the variables shown below.
Obviously, if someone wishes to confirm your public key's fingerprint, you can complete the same command on your own key as shown below.
"Your Name" keys fingerprint has been highlighted above.
If you now trust you have the correct public key you can sign the key to show that you trust the key to belong to "Your Mate". The command to sign a key is "gpg --sign-key Your.Mate@email.com"
By signing other peoples keys, you can set up a ring of trust. Other people may choose to trust a key on the basis of your signiture.
So now for the fun part. We have installed gpg, created our own key, exported our public key to some one, and now we have imported "Your Mate" public key. We are finally ready to encrypted our first message.
In order to remain in CLI, I have created a short text message using "cat" as shown below.
When using a "cat >" to create a text file, you need to press "CTRL+D" to exit the redirect.
You could use a text editor like gedit or Vi if you prefer.
You can also use "cat" to check the contents of your file as shown below.
We now have a text file called message.txt in our home directory.
This file can be encrypted using gpg, but lets first consider what we need.
1) the text file
2) the public key of the recipient
3) to make the file ASCII we need to include the "--armor" command.
The required command should look something like this;
"gpg --recipient Your.Mate@email.com --armor --encrypt message.txt"
So with this information we can encrypt the file as shown below
Notice we now have a "message.txt.asc" file. This is the encrypted file.
Also notice the orginal "message.txt" file still exists! If this contains sensitive data, it should be removed.
Check the contents of your encrypted file using the cat command as shown below.
You can now send this information via email, or any other method safe in the knowledge that it will only be read by its intended recipient/s
You can encrypt a message to more than one recipient including yourself.
That concludes this blog.
You will also have generated a PGP key and exported the Public Key.
If not, please read the previous blogs installing pgpgpg and exporting public key
This blog aims to explain how to import someone else's key, and then send them an encrypted message.
Before we progress any further, you need to have someones Public Key. This can be acquired by email, downloading of a website, or passed via any means, but it is important that you trust the public key you have is from who you think it is from.
I have acquired a public key from "Your Mate" and have it in my home folder.
I first check the contents of my Key ring using the "gpg --list-key" command as shown below.
If you've been following my blogs in order, you should find the only key you have is the one you've generated.
Import the public key for the person you wish to send the encrypted message to with the "gpg --import keyname" command as shown below. As you can see, the key I imported was called "YourMate.asc"
You can confirm the key is now on your keyring by repeating the "gpg --list-key" command as shown above. Notice you now have the "Your Mate" key.
You can check that you have imported the correct public key by asking the owner to confirm the keys finger print.
This can be done using the "gpg --fingerprint" command to see all your keys fingerprints, or an individual key using any of the variables shown below.
Obviously, if someone wishes to confirm your public key's fingerprint, you can complete the same command on your own key as shown below.
"Your Name" keys fingerprint has been highlighted above.
If you now trust you have the correct public key you can sign the key to show that you trust the key to belong to "Your Mate". The command to sign a key is "gpg --sign-key Your.Mate@email.com"
By signing other peoples keys, you can set up a ring of trust. Other people may choose to trust a key on the basis of your signiture.
So now for the fun part. We have installed gpg, created our own key, exported our public key to some one, and now we have imported "Your Mate" public key. We are finally ready to encrypted our first message.
In order to remain in CLI, I have created a short text message using "cat" as shown below.
When using a "cat >" to create a text file, you need to press "CTRL+D" to exit the redirect.
You could use a text editor like gedit or Vi if you prefer.
You can also use "cat" to check the contents of your file as shown below.
We now have a text file called message.txt in our home directory.
This file can be encrypted using gpg, but lets first consider what we need.
1) the text file
2) the public key of the recipient
3) to make the file ASCII we need to include the "--armor" command.
The required command should look something like this;
"gpg --recipient Your.Mate@email.com --armor --encrypt message.txt"
So with this information we can encrypt the file as shown below
Notice we now have a "message.txt.asc" file. This is the encrypted file.
Also notice the orginal "message.txt" file still exists! If this contains sensitive data, it should be removed.
Check the contents of your encrypted file using the cat command as shown below.
You can now send this information via email, or any other method safe in the knowledge that it will only be read by its intended recipient/s
You can encrypt a message to more than one recipient including yourself.
That concludes this blog.
Friday, 30 March 2012
Exporting a GPG public key in linux CLI
If you read my previous blog pgp using gpg , your probably thinking... "Well now what do I do with my key..?"
If so, this blog is for you!
First, a little bit about PGP usage. You have two keys, the secret key and the public key.
The public key is the one you can share freely, the secret key you should protect.
If someone wants to send you an encrypted message, they first need to get your public key.
If you want to send someone an encrypted message, you first need to get there public key.
To display you key in ASCII type the "gpg --export -armor <key name>" command. This will display the key in the CLI session, but you would need to cut and paste the contents to a text file. This process can be completed quicker by redirecting the output of the command direct to a text file using the ">" meta character as shown below.
Now when we type "ls" to list the files in our home directory we see a file called "YourName.asc" which is a text file containing your public key.
Incidently, I chose ".asc" as I know this is what PGP uses to identify public keys.
You can check the contents of the file by opening it in a text editor like gedit, but if we want to stay in CLI we could use "cat filename" or to enable scrolling you can type "less filename" as shown below.
To exit less, use the ":Q"
command as you would in Vi.
The contents of the file look like this;
This is the public key for "YourName" and can be distributed in any way you choose, including email.
The contents of the file look like this;
-----BEGIN PGP PUBLIC KEY BLOCK-----
Version: GnuPG v1.4.10 (GNU/Linux)
Version: GnuPG v1.4.10 (GNU/Linux)
mQENBE90JBkBCADEaja/iOtuN0eI/ZNchzxgmOBsHUhcPwl/ndAifQfAgCbU/Ld+
toLgkuVHtocDq98XOyS77QDTSrDyMG66sVcr3Ok+Lg8KOZJLoGjp67H2gIymFbRp
0Tkv2K3sfJJ8eqwF+5fkKP2FFjOBDqE6gioOKF1EZpNJkdhFlrYviwjnmYxGP2N7
po45N7UGthUJyD1gE3AzALcWc1QJWyLMBLRsItNgBcrjvUCMg/gSP+AtZViwfMAj
4WtinhQ0KIV5Wi8rMf9eQEquV2PEX1edM0+GE0dHSYst3kcmvl0hm7/yGsSUcEt+
Gb9YhYa3biJ9WY6A7Pod1+YO3Zb3lcJYLWsNABEBAAG0L1lvdXIgTmFtZSAoWW91
ciBOaWNrbmFtZSkgPFlvdXIuTmFtZUBlbWFpbC5jb20+iQE4BBMBAgAiBQJPdCQZ
AhsDBgsJCAcDAgYVCAIJCgsEFgIDAQIeAQIXgAAKCRAO/fSWlRUP1UZ0B/9YymIu
gEoGBOeJ2QdUpOzxFFPTnv9xD2D8Lu5XQZaR2fXXXhCIUsOtwOnbp6AWo74VKkoU
a0oDPbB34A42mcQODoCsHfJubgqYFHbkon0AG9THaH2f5OQ1Q0Ka2U74PioKal1P
Yqzek4gyGcOUniYXol9v7I/AAzlNidiFl2nHGGmvv90lidT4tO6R6eGI/b4Zpvlc
8gBZMt/H2+ZMSCiICZfI2d4jUm0pr7Zna6JfTBR8QMQBbieNq0o/uyxkYLmexffC
RXpEAVnvCKRLjJPeag9jZyjg7kvosJIJdKBo7cOV9jHVjmyQjsSUFYZT4KxVxFH3
P70/Pr8Trm+Ctx+RuQENBE90JBkBCADqB01wfMCgqmdPWsOHm61kc1UMV7puaqNl
id/VHwkRk8XXqgN1wSInA8BpY+MGommqieoEJdp7XtPRQkrMgS+m3B2NRpFPoGq3
ehsW+LaKTXHAWeIquNLXI8BCvPrSQDSm6WLIBjiywPOID3+5vbHmFAKq3+On6ial
ZrAlVj4CE7jPb7iqLAfG95KCiBQZto+0cYTilMRs4XcKKCoXT2JOxl5G4kUxp9Jq
IHEHZnePMc9KYaTG74dUehimyoyKbBriLrQjB2qwzoMf9jCJRJBYdpUvjqMIdFOO
IeLTOHUvNXDFWIb9ZioOEQTSc75vHvFsJeS6M2SfWp1lO8V7i6gdABEBAAGJAR8E
GAECAAkFAk90JBkCGwwACgkQDv30lpUVD9VMiAgAwx27TgKHBW0Ofv4a64vBBGDu
u8JL4/wX7BYa+uBHvbMYoqZMpzzcEwIbwGXuISRqufcFt85VtwhbNGsFeuoMNJcx
ggWjniQ6z4nTU+0ppAoovmvNhQIqs+45iQ0qDDMFTQSUX4kRnMeV3peT/gqAfXjG
iS7tlj6wK0pAjyPsme2JxiRTt1CB7kiSkqEoQsHoTPBejt7AlKmbR5lfnmZP6yRp
Bj5JSMlj+0FZqNFcLFEgRXNR7SGhR2VQWTzIg9pwek6QaWRi7M0sLzGVDpka08Xo
mPKlCboX6p3ZN1io6hKywi/9498PR1oBamz9md4GB7B+aAQ/c5QYDjEbUnCwJQ==
=MgSk
-----END PGP PUBLIC KEY BLOCK-----
toLgkuVHtocDq98XOyS77QDTSrDyMG66sVcr3Ok+Lg8KOZJLoGjp67H2gIymFbRp
0Tkv2K3sfJJ8eqwF+5fkKP2FFjOBDqE6gioOKF1EZpNJkdhFlrYviwjnmYxGP2N7
po45N7UGthUJyD1gE3AzALcWc1QJWyLMBLRsItNgBcrjvUCMg/gSP+AtZViwfMAj
4WtinhQ0KIV5Wi8rMf9eQEquV2PEX1edM0+GE0dHSYst3kcmvl0hm7/yGsSUcEt+
Gb9YhYa3biJ9WY6A7Pod1+YO3Zb3lcJYLWsNABEBAAG0L1lvdXIgTmFtZSAoWW91
ciBOaWNrbmFtZSkgPFlvdXIuTmFtZUBlbWFpbC5jb20+iQE4BBMBAgAiBQJPdCQZ
AhsDBgsJCAcDAgYVCAIJCgsEFgIDAQIeAQIXgAAKCRAO/fSWlRUP1UZ0B/9YymIu
gEoGBOeJ2QdUpOzxFFPTnv9xD2D8Lu5XQZaR2fXXXhCIUsOtwOnbp6AWo74VKkoU
a0oDPbB34A42mcQODoCsHfJubgqYFHbkon0AG9THaH2f5OQ1Q0Ka2U74PioKal1P
Yqzek4gyGcOUniYXol9v7I/AAzlNidiFl2nHGGmvv90lidT4tO6R6eGI/b4Zpvlc
8gBZMt/H2+ZMSCiICZfI2d4jUm0pr7Zna6JfTBR8QMQBbieNq0o/uyxkYLmexffC
RXpEAVnvCKRLjJPeag9jZyjg7kvosJIJdKBo7cOV9jHVjmyQjsSUFYZT4KxVxFH3
P70/Pr8Trm+Ctx+RuQENBE90JBkBCADqB01wfMCgqmdPWsOHm61kc1UMV7puaqNl
id/VHwkRk8XXqgN1wSInA8BpY+MGommqieoEJdp7XtPRQkrMgS+m3B2NRpFPoGq3
ehsW+LaKTXHAWeIquNLXI8BCvPrSQDSm6WLIBjiywPOID3+5vbHmFAKq3+On6ial
ZrAlVj4CE7jPb7iqLAfG95KCiBQZto+0cYTilMRs4XcKKCoXT2JOxl5G4kUxp9Jq
IHEHZnePMc9KYaTG74dUehimyoyKbBriLrQjB2qwzoMf9jCJRJBYdpUvjqMIdFOO
IeLTOHUvNXDFWIb9ZioOEQTSc75vHvFsJeS6M2SfWp1lO8V7i6gdABEBAAGJAR8E
GAECAAkFAk90JBkCGwwACgkQDv30lpUVD9VMiAgAwx27TgKHBW0Ofv4a64vBBGDu
u8JL4/wX7BYa+uBHvbMYoqZMpzzcEwIbwGXuISRqufcFt85VtwhbNGsFeuoMNJcx
ggWjniQ6z4nTU+0ppAoovmvNhQIqs+45iQ0qDDMFTQSUX4kRnMeV3peT/gqAfXjG
iS7tlj6wK0pAjyPsme2JxiRTt1CB7kiSkqEoQsHoTPBejt7AlKmbR5lfnmZP6yRp
Bj5JSMlj+0FZqNFcLFEgRXNR7SGhR2VQWTzIg9pwek6QaWRi7M0sLzGVDpka08Xo
mPKlCboX6p3ZN1io6hKywi/9498PR1oBamz9md4GB7B+aAQ/c5QYDjEbUnCwJQ==
=MgSk
-----END PGP PUBLIC KEY BLOCK-----
This is the public key for "YourName" and can be distributed in any way you choose, including email.
This also achieves my
objective for this blog. In my next blog I hope to demonstrate how to use other
peoples public keys to encrypt a message.
Thursday, 29 March 2012
PGP using GPG.... ;o)
Gpg is stands for Gnu Privacy Guard and is a free alternative to the PGP cryptographic software.
GnuPG (or GPG) follows the RFC 4880 which is the standard specification of OpenPGP. The most important thing GPG is interoperable with PGP. GPG is build as a command line utility but also have several front-ends for KDE, Gnome and other Linux desktops, but also is directly integrated in other software like: Email Clients as Mozilla Thunderbird, Evolution, Kmail, Instant Messaging as PSI, Fire, Browsers as Mozilla Firefox etc.
Installing GPG
sudo apt-get install pgpgpg
Generating key pairs
The basis of PGP encryption is you generate a key pair. This comes in two parts, a Secret Key and a Public Key. The Public Key you can upload to key servers or distribute via any means you like. (I have a copy of one of my keys on the public space of my Dropbox account)
Run “gpg –gen-key” and just follow the steps. An example of output is presented on following lines
Next you will be asked some details about the key! In order for
people to be able to find your key on a key server, GPG ask for "Real
name". I like to think that people could get your key via your email
address, and if I want to send something to someone encrypted, i would
prefer to get there current public key direct from them.Supply
the details required, I have generated the key above to show you what
format the key will take. When complete, press "O" and enter to generate
the key.
Your key will now be generated. At this stage I like to run my mouse around the screen to generate as much random data as I can...The time taken for the key generation varies depending on the key size, and how much random data you generate.
When your key is finished generating the key fingerprint will be displayed as shown above.You can also check the keys on your keyring with the "gpg --list-key" command as shown below.
You can also check your keys fingerprint with the "gpg --fingerprint <name>" command.
As you can see from my screenshot below, I have found the key on all three sections of the name.
The first command was looking for the nickname (Your Nickname)
The second was searching on the Key name (Your Name)
The last command used the email address supplied (Your.Name@email.com)
I have also highlighted the keys fingerprint.
This concludes my fist blog on PGP. At this stage all we have done is installed the packaged and generated our own key in Linux and from the command line (CLI).
If you have any further questions, please feel free to ask Google! ;o)
GnuPG (or GPG) follows the RFC 4880 which is the standard specification of OpenPGP. The most important thing GPG is interoperable with PGP. GPG is build as a command line utility but also have several front-ends for KDE, Gnome and other Linux desktops, but also is directly integrated in other software like: Email Clients as Mozilla Thunderbird, Evolution, Kmail, Instant Messaging as PSI, Fire, Browsers as Mozilla Firefox etc.
GnuPG encrypts messages using asymmetric keys. This keys are
generated by the users and are exchanged with others through TRUSTED key
servers.GPG also knows symmetric key cryptography.
sudo apt-get install pgpgpg
Generating key pairs
The basis of PGP encryption is you generate a key pair. This comes in two parts, a Secret Key and a Public Key. The Public Key you can upload to key servers or distribute via any means you like. (I have a copy of one of my keys on the public space of my Dropbox account)
Run “gpg –gen-key” and just follow the steps. An example of output is presented on following lines
You now need to select your key type. RSA is the default, to select RSA type "1" and press enter.
Then choose your key size. The default key size is 2048. Many people think a larger key is more secure than a smaller key, there is some truth in this, but it will also be larger, making your encrypted files larger.
Statistically, you are far better off having a 2048 bit key with a strong and longer pass phrase than a 4096 bit key with a poor pass phrase. I sit firmly in the stronger pass phrase camp, and just generate 2048 bit keys.
Next you will be asked how long you want the key to remain valid. This is a nice feature if you want your keys to expire after a fixed time. For the purposes of this blog, I'm going to create a key which won't expire as shown above.
Your key will now be generated. At this stage I like to run my mouse around the screen to generate as much random data as I can...The time taken for the key generation varies depending on the key size, and how much random data you generate.
When your key is finished generating the key fingerprint will be displayed as shown above.You can also check the keys on your keyring with the "gpg --list-key" command as shown below.
You can also check your keys fingerprint with the "gpg --fingerprint <name>" command.
As you can see from my screenshot below, I have found the key on all three sections of the name.
The first command was looking for the nickname (Your Nickname)
The second was searching on the Key name (Your Name)
The last command used the email address supplied (Your.Name@email.com)
I have also highlighted the keys fingerprint.
This concludes my fist blog on PGP. At this stage all we have done is installed the packaged and generated our own key in Linux and from the command line (CLI).
If you have any further questions, please feel free to ask Google! ;o)
Wednesday, 28 March 2012
%Error opening tftp://255.255.255.255/network-confg (Socket error)
Occasionally, during bootup of Cisco hardware through Cisco IOS software,
error messages similar to these are displayed:
-
%Error opening tftp://255.255.255.255/network-confg (Socket error)
-
%Error opening tftp://255.255.255.255/cisconet.cfg (Socket error)
-
%Error opening tftp://255.255.255.255/3620-confg (Socket error)
-
%Error opening tftp://255.255.255.255/3620.cfg (Socket error)
These error messages are related to the default service configuration
option built into Cisco IOS software, which attempts to access the service
configuration files from a network Trivial File Transfer Protocol (TFTP)
server.
In order to disable this feature, issue the no service config global
command.
Router#config terminal Enter configuration commands, one per line. Router(config)#no service config Router(config)#exit Router#copy running-config startup-config
These error messages no longer appear at the next bootup of the
router.
Friday, 2 March 2012
A quick guide to setting up a TFTP server in Ubuntu
The aim of this guide
is to describe the process required to setup a TFTP server on a Linux
PC. The main reason I
require a TFTP server is for backing up configuration files and IOS's
from Cisco devices.
Trivial File Transfer Protocol (TFTP) is a simple protocol to transfer files. It has been implemented on top of the User Datagram Protocol
(UDP) using port number 69. TFTP is designed to be small and easy to
implement, therefore, lacks most of the features of a regular FTP. TFTP
only reads and writes files (or mail) from/to a remote server. It cannot
list directories, and currently has no provisions for user
authentication.
There are plenty of free TFTP server daemons available for download for Windows machines, but at home I run Linux, and wanted to setup a dedicated machine just for copying Cisco IOS's and configs onto.
TFTP is far from secure, so I do NOT recommend leaving this port open on a machine which has access to the Internet.
Also it should be noted
that this guide is intentionally command line as that is where the
magic happens!
I normally sudo su
which will log you in with root privileges and prevent you from
continually entering your password.
This is not best practice, but its my guide and I'm lazy. If you prefer, insert a “sudo” in front of every command and skip the sudo su command.
This will install the serversudo suapt-get update && apt-get install tftp-hpa tftpd-hpa
The default location
for for TFTP files is /var/lib/tftpboot. You can set a different
location later if you'd like, but you must chmod and chown
the directory you choose.
sudo mkdir /var/lib/tftpbootsudo chown nobody.nogroup /var/lib/tftpbootsudo chmod 777 /var/lib/tftpboot
Edit the TFTP server configuration file to put the service in daemon mode and set a custom directory you may have chosen above.
You can do this using command line text editors like Vi or Emacs but I just use Gedit
You can do this using command line text editors like Vi or Emacs but I just use Gedit
gedit /etc/default/tftpd-hpa
This is where you can
customise you TFTP server.
I chose to create my
servers root directory in my home directory.
In my case that is
/home/anon/
I called my root directory TFTProot.
I called my root directory TFTProot.
So my tftpd-hpa file looks like this;
# /etc/default/tftpd-hpa
RUN_DAEMON="yes"
OPTIONS="-l -s /home/anon/TFTProot"
TFTP_USERNAME="tftp"
TFTP_DIRECTORY="/home/anon/TFTProot"
TFTP_ADDRESS="0.0.0.0:69"
TFTP_OPTIONS="--secure
RUN_DAEMON="yes"
OPTIONS="-l -s /home/anon/TFTProot"
TFTP_USERNAME="tftp"
TFTP_DIRECTORY="/home/anon/TFTProot"
TFTP_ADDRESS="0.0.0.0:69"
TFTP_OPTIONS="--secure
Save the file and then be sure to create the directory required;
mkdir /home/anon/TFTProotchown anon.anon /home/anon/TFTProotchmod 777 /home/anon/TFTProot
As your logged in as
root, the directory will also belong to root so chown the directory
to your login account and group.
I also made the
directory world rightable.. (probably not best practice, but it
worked for me and avoided the dreaded “TFTP error 1”)
Once my directory
structure was in place I restarted the daemon;
/etc/init.d/tftpd-hpa restart
You should now have a
working TFTP server up and running.
Don't take my word for
it, check...
netstat
-a |grep tftpudp
0 0 *:tftp
*:*
Or another way to check would be to scan your PC. You can scan the loopback IP address using nmap like this;
nmap
-sU 127.0.0.1
Starting
Nmap 5.21 ( http://nmap.org ) at 2012-01-31 21:17 GMT
Nmap
scan report for localhost.localdomain (127.0.0.1)
Host
is up (0.13s latency).
Not
shown: 994 closed ports
PORT
STATE SERVICE
68/udp
open|filtered dhcpc
69/udp
open|filtered tftp
135/udp
open|filtered msrpc
A few notes about usage.
Before you can send a file to the tftp server, it needs to exist in the tftp directory.
I'm not sure why, or if I'm doing something wrong, but I found the secret to a successful transfer is to create a empty file first.
I'm not sure why, or if I'm doing something wrong, but I found the secret to a successful transfer is to create a empty file first.
touch filenamechmod 777 /home/anon/TFTProot/filenamels -al-rwxrwxrwx 1 root root 0 2012-01-31 21:37 filename
Incidentally, if anyone
reading this knows of a better way, I would be intrigued to know how?
It is at this point we
are ready to send the file from our Cisco device;
router#copy run tftp Address or name of remote host[]?192.168.2.2 Destination filename [router-config]? filename !! 3974 bytes copied in 1.492 secs (2664 bytes/sec) router#
At this point your running-config should be in the directory you've created.
Subscribe to:
Comments (Atom)